
Review Article
Austin J Forensic Sci Criminol. 2023; 10(2): 1097.
Quality Assurance in Digital Forensic Investigations: Optimal Strategies and Emerging Innovations
Anwaar Iftikhar*; Rida Farooq; Mehvish Mumtaz; Sana Hussain; Mubeen Akhtar; Muhammad Ali; Ghulam Zahara Jahngir
Centre for Applied Molecular Biology, University of Punjab, Lahore, Pakisthan
*Corresponding author: Anwaar Iftikhar Centre for Applied Molecular Biology, University of Punjab, Lahore, Pakisthan. Email: anwaariftikhar33@gmail.com
Received: August 17, 2023 Accepted: September 29, 2023 Published: October 06, 2023
Abstract
Digital forensic investigations are critical in modern law enforcement, cybersecurity, and legal proceedings. Ensuring digital evidence’s accuracy, integrity, and reliability is paramount in these contexts. This review article explores the challenges and best practices associated with quality control in digital forensic investigations and the emerging technologies that are reshaping the field.
The article begins by discussing the foundational concepts of quality control in digital forensics, emphasizing the need for standardized procedures, documentation, and validation techniques. It delves into the potential sources of errors and bias that can arise during the acquisition, preservation, analysis, and presentation of digital evidence. It highlights the importance of continuous monitoring and review to mitigate these risks.
The review article further examines the evolving landscape of digital forensic tools and technologies advancing quality control efforts. It covers advancements in data acquisition methods, including live forensics and memory analysis, and discusses the role of artificial intelligence and machine learning in automating quality control processes. The integration of Blockchain and cryptographic techniques for ensuring the integrity of digital evidence is also explored. In addition, the article addresses the challenges and opportunities presented by cloud computing, IoT devices, and the proliferation of digital data sources. It emphasizes adaptability and agility in quality control approaches to accommodate the changing digital landscape.
Through a comprehensive analysis of established practices and emerging technologies, this review article offers practitioners, researchers, and policymakers’ insights into enhancing the reliability and trustworthiness of digital forensic investigations. By adopting robust quality control measures and embracing innovative technologies, the digital forensics community can ensure its findings hold up to scrutiny in the courtroom and beyond.
Introduction
In today's technology-driven world, digital forensic investigations are fundamental, while digital evidence is significant in settling legal disputes and investigating crimes. Politt refers to the period before 1985 as pre-history and characterizes the history of Digital Forensics (DF) as brief yet complicated [1]. Individual computer enthusiasts inside law enforcement and government organizations began sharing the information that could be gleaned from the new personal computers at the beginning of the 1980s. The DF field was initially known as computer forensics for a long time. Exams were performed at desks and other available locations instead in a lab setting during the beginning of the discipline, which instead began in offices and basements [2]. The discipline gradually changed due to the Internet, data carriers, and several other technical advancements. The demand for precise and trustworthy digital forensic investigations increases as our reliance on digital devices rises. To safeguard the ideals of justice and preserve the integrity and admissibility of the evidence, it is crucial to provide quality control in these investigations [3]. Digital forensic techniques usually involve assessing the strategy, selecting the tool(s), doing quality checks, and producing reports. It is not inherently controversial to ensure that digital forensics, like all other types of forensic science, is supplied to the proper degree of quality for its usage in a CJS [4]. A good and thorough Digital Forensics (DF) process depends on the consecutive DF phases, each of which depends on the sequential DF procedures, which depend on the tasks and subtasks that make up each procedure. The Forensic Science Regulator, a government-funded organization operating inside the judicial system in the UK, was founded in 2007 [5]. In digital forensic investigations, quality control refers to the systematic steps and techniques to ensure that the investigation procedures, methods, and findings are accurate, dependable, and consistent. Standard operating protocols, evidence management and preservation, documentation, validation and verification, peer review, and ongoing professional development are all used in the strategy [6]. DF quality control measures will cover new and established technologies, such as remote storage, computing, imaging, image comparison, video processing and enhancement (including CCTV), audio analysis, satellite navigation, and communications systems [7].
The Forensic Science Regulator ensures that a suitable regime of scientific quality standards is applied to the delivery of forensic science services across the criminal justice system to obtain accurate and trustworthy outcomes in digital forensics. The reliability of digital evidence may substantially influence how criminal and civil cases are resolved and how regulations are enforced [8]. Adherence to strict quality control measures strengthens the admissibility of digital evidence in court. In legal systems, evidence must adhere to particular criteria to be acceptable. Digital forensic professionals may show the dependability, validity, and chain of custody of digital evidence by putting quality control procedures in place, increasing the likelihood that courts will accept it as evidence [9]. Organizations and regulatory organizations emphasize the necessity of quality control in digital forensic investigations, including the Scientific Working Group on Digital Evidence (SWGDE) and the International Organization on Computer Evidence (IOCE). To ensure that investigations are carried out fairly, impartially, and without prejudice, it aids in the establishment of a clear and transparent approach [10].
Organizations may increase the reliability and trustworthiness of their investigative practices by putting quality control systems in place. The validity of digital forensic investigations directly impacts public trust in the legal system. Strong quality control procedures show a dedication to responsibility and openness [11]. It promotes trust in law enforcement organizations, forensic experts, and the legal system when the public trusts the validity of digital evidence and the investigation process [12]. Quality control is crucial for digital forensic investigations to provide accurate, trustworthy, and defendable results. Practitioners can protect professional standards, improve the admissibility of digital evidence, and preserve the public's trust in the objectivity of the investigation process by applying strict quality control methods [13]. The value of following best practices, standardizing procedures, and the function of accreditation and certification organizations in assuring the calibre of digital forensic investigations. The influence of cloud computing, encryption technology and the difficulties of network-based investigations will all be explored as new quality control concerns [14]. This review paper examines the present level of quality control in digital forensic investigations to offer useful information to practitioners, academics, policymakers, and legal experts who work in digital forensics [15]. It emphasizes how crucial it is to put strict quality control procedures in place to guarantee the precision, dependability, and integrity of digital evidence and increase the legitimacy of digital forensic techniques in the judicial system [16]. This in-depth analysis of quality control in digital forensic investigations will help to illuminate the difficulties, ideal procedures, and developments in this important area [17]. This article aims to contribute to the continued development and standardization of digital forensic practices, eventually boosting the usefulness and reliability of digital evidence in judicial proceedings by fostering a complete awareness of quality control processes. The ongoing development and standardization of quality control procedures in digital forensics facilitate the effective and trustworthy use of digital evidence in judicial proceedings.
Historical Perspective of Digital Forensic Investigations
Computer forensics, often digital forensics, was initially introduced in 1970 [18]. The initial inquiry uses the suspect's computer to demonstrate the financial fraud. In 1996, there was a report of the first computer crime to go to court. Computer crimes are those in which computer use facilitates and is the primary cause of the offence [19]. In 1996 [20], the first computer crime to be prosecuted in Texas, USA, led to a 5-year sentence. With the rise in popularity of computers and the Internet in 1990, digital crimes involving computers began to increase. In the late 1990s and early 2000s, computer forensics emerged independently. According to CSI polls, about 46% of respondents were victims of cyber crimes of some form [21]. According to a 2010 Gallup survey, 11% of American adults become victims of online or computer-related crimes in their homes. This ratio is 6-8% higher than seven years ago. According to a poll by "The Australian Company Crime Survey" [22], financial theft and data breaches cost A$ 2,000,000 in 2006. According to a company crime survey, financial theft and data breaches cost Australia an estimated A$ 2,000,000 in lost income. With new digital technologies' introduction and increasing use for investigative purposes, the phrase "digital forensic" is now utilized - Figure 1.
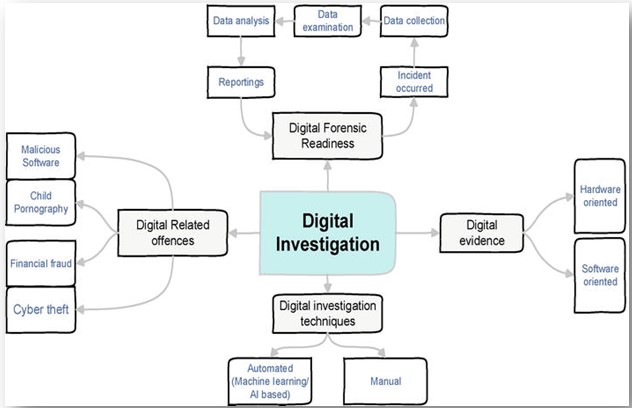
Figure 1: Taxonomy of digital investigations.
Best Practices for Ensuring Quality Control in Digital Forensic Investigations
Digital forensic investigations are crucial in modern law enforcement and legal proceedings. However, ensuring the quality and reliability of the evidence collected is essential to support the successful resolution of cases. This review article explores a set of best practices aimed at maintaining high-quality standards throughout the digital forensic investigative process [23].
Pre-Investigation Planning
Allocate sufficient resources for thorough and efficient investigations, including skilled personnel, specialized tools, and equipment. Develop and adhere to comprehensive SOPs that outline the step-by-step procedures for evidence handling, preservation, and analysis. Establish and maintain a secure chain of custody to track the handling and transfer of evidence, ensuring its admissibility in court [24].
Evidence Collection and Preservation
Utilize a systematic and methodical approach to identify and collect potential digital evidence, ensuring all relevant data sources are considered. Use validated and forensically sound tools to extract, preserve, and handle digital evidence to prevent data contamination or alteration. Thoroughly document the evidence collection process, including date, time, location, and individuals involved, to provide a clear audit trail [25].
Data Analysis
Verify the integrity and authenticity of the acquired data through hash values and digital signatures to ensure the accuracy of the analysis. Encourage peer review of analysis findings to validate conclusions and reduce the risk of errors or biases. Engage qualified and experienced digital forensic analysts to conduct in-depth analysis and interpret complex digital evidence accurately [26].
Reporting
Prepare detailed and precise reports, including the methodology, findings, and conclusions, to facilitate easy understanding by stakeholders. To maintain transparency and credibility, provide full disclosure of any limitations, assumptions, or uncertainties associated with the investigation. Use language and terminology accessible to non-technical audiences, including legal professionals and jurors [27].
Quality Assurance
Conduct regular internal audits of the digital forensic processes to identify potential weaknesses and areas for improvement. Provide ongoing training and professional development opportunities for forensic analysts to keep them updated on evolving technologies and methodologies [28].
Legal and Ethical Considerations
Ensure compliance with applicable laws, regulations, and ethical guidelines governing digital forensic investigations. Respect the privacy rights of individuals whose data is subject to the inquiry and adhere to strict data protection principles [29].
Collaboration and Communication
Foster collaboration between digital forensic teams, law enforcement, legal professionals, and cybersecurity experts to enhance the effectiveness of investigations. Maintain open and effective communication channels among team members and stakeholders throughout the analysis [30].
Documentation and Records Management
Utilize a robust case management system to track and organize all aspects of the investigation, including evidence, correspondence, and analysis. Ensure proper and secure retention of all documentation and records related to the quest for future reference and legal requirements [31].
Post-Investigation Review
Conduct post-investigation reviews to evaluate the investigative process's effectiveness and identify improvement areas. Incorporate lessons learned from previous investigations into future procedures to enhance the overall quality of digital forensic practices. Implementing best practices in digital forensic investigations is essential to ensure the collected evidence's accuracy, reliability, and integrity. By adhering to these guidelines, digital forensic teams can strengthen the credibility of their findings and contribute to more successful outcomes in legal proceedings and criminal investigations [32].
Quality Control Frameworks and Standards in Digital Forensics
Digital forensics is a critical discipline in modern-day investigations, and ensuring the quality of evidence is paramount for successful legal outcomes. Quality control frameworks and standards are essential for maintaining rigorous practices throughout the digital forensic process [33].
ISO/IEC 17025: 2017 - General Requirements for the Competence of Testing and Calibration Laboratories
ISO/IEC 17025: 2017 is a critical standard that provides a framework for ensuring the competence and credibility of testing and calibration laboratories, including those involved in digital forensics. By implementing the principles and requirements of this standard, digital forensic laboratories can enhance the accuracy and reliability of their investigative processes, ultimately contributing to more robust and credible evidence in legal cases [34].
Management requirements: Explaining the need for laboratories to establish and maintain a robust QMS to manage and control all aspects of their operations. Highlighting the requirements for effective document control, ensuring the availability and validity of relevant documents. Addressing the responsibilities of laboratory management in ensuring personnel competence, impartiality, and effective decision-making. Discussing the importance of comprehensive review processes for requests, tenders, and contracts to meet customer requirements. Emphasizing the significance of competent and qualified personnel in conducting testing and calibration activities. Outlining the requirements for calibrating equipment used in testing and calibration processes to ensure accuracy and reliability. Discussing the need to establish and maintain traceability of measurements to national or international standards [35].
Conformity Assessment and Reporting:
Explaining the importance of ensuring test results' validity and reliability, including correctly reporting uncertainties. Addressing the methods for assessing conformity and using appropriate statistical techniques. Highlighting the requirements for clear and accurate reporting of test and calibration results to customers. Discussing the role of internal audits in assessing the effectiveness of the QMS and identifying areas for improvement. Emphasizing the importance of implementing corrective actions to address non-conformities and improve processes [36].
Application to Digital Forensics Laboratories: Demonstrating the applicability of ISO/IEC 17025:2017 to digital forensics laboratories and its significance in maintaining competence and reliability. Discussing how adherence to the standard can enhance the admissibility of digital forensic evidence in legal proceedings [37].
SWGDE (Scientific Working Group on Digital Evidence) Best Practices
The Scientific Working Group on Digital Evidence (SWGDE) is an esteemed organization dedicated to establishing best practices in the field of digital forensics. This paper comprehensively reviews the SWGDE's best practices, which provide authoritative guidelines for conducting digital forensic investigations. The SWGDE's recommendations cover various aspects of the investigative process, including evidence collection, analysis, reporting, and quality assurance.
By adhering to these best practices, digital forensic practitioners can ensure the integrity and reliability of their findings, enhance cross-disciplinary collaboration, and contribute to more successful outcomes in legal proceedings. The SWGDE is a leading organization focused on promoting best practices in digital forensics investigations [38].
NIST (National Institute of Standards and Technology) Guidelines
The National Institute of Standards and Technology (NIST) is a renowned authority in setting standards and guidelines for various fields, including digital forensics. This paper comprehensively reviews the NIST guidelines relevant to digital forensics investigations [39]. The NIST guidelines cover various topics, including data acquisition, analysis, reporting, and incident response. Additionally, the paper explores the NIST Special Publication 800-86, which focuses on integrating digital forensics within incident response procedures. By adhering to the NIST guidelines, digital forensic practitioners can enhance their investigations' accuracy, reliability, and efficiency, ultimately contributing to more effective outcomes in criminal and cyber security incidents [40].
Emerging Technologies in Quality Control for Digital Forensic Investigations
As digital forensics plays an increasingly critical role in modern investigative practices, the need for robust quality control measures becomes paramount. This paper explores emerging technologies that potentially revolutionize quality control in digital forensic investigations. From automated evidence acquisition and analysis tools to advanced data validation techniques, these technologies enhance accuracy, efficiency, and reliability in the investigative process [41]. The article also discusses the challenges and considerations associated with implementing emerging technologies in quality control. It emphasizes integrating human expertise with technological advancements to ensure optimal results in digital forensic investigations. Data from various sources, including books, videos, pictures, and medical information, is increasingly transformed into digital formats. This has made us vulnerable to cybercrimes.
The digital forensic investigation aims to recover lost or intentionally deleted files from suspects [42]. However, current methods require human interaction, slowing down the process. Machine Learning (ML) and automation can help investigate digital crimes more efficiently. This chapter aims to research machine learning-based digital forensic investigation, identify gaps, and address challenges and open issues in this field. The Digital Forensic Research Workshop (DFRWS) has Defined Digital Forensics (DF) as "The use of scientifically derived and proven methods toward the preservation, collection, validation, identification, analysis, interpretation, documentation and presentation of digital evidence derived from digital sources to facilitate or further the reconstruction of events found to be criminal, or helping to anticipate unauthorized actions shown to be disruptive to planned operations" [43].
Demands from DF are becoming more significant today. DF investigation techniques assist in gathering crucial data from the infected device. Businesses today rely heavily on the Internet and digital gadgets. Equally important is getting the essential evidence from these devices. It is necessary to obtain digital evidence from the system to confirm or refute any investigator's theories regarding the incident. [44].
Artificial Intelligence (AI), Machine Learning (ML) and Deep Learning
It's critical to consider how AI, ML, and Deep Learning (DL) approaches might genuinely assist in resolving DF issues and how these approaches differ.
Artificial intelligence: The ability of machines to carry out human activities, such as image recognition, natural language processing, etc., is known as Artificial Intelligence (AI). The key idea is that artificial intelligence is not machine learning or intelligent objects. One way to think of artificial intelligence is as a tool that can carry out human jobs and make them simple. AI technology is greatly expanding, dramatically increasing the incidence of malicious activity [45]. Intelligent agent refers to artificial intelligence software. Environment-interacting intelligent agents are used. The agent employs a method to recognize environments using its sensors, after which it can act to change a state using those same sensors [46]. The crucial components of AI technologies are how input is gathered from sensors and mapped to actuators so that the agents' internal processes can carry out these effects. Creating a machine that behaves exactly like a human being is the ultimate objective of AI. This work can be completed by utilizing solely the learning algorithms intended to create a sketch of the learning’s of the human brain. AI technologies offer many benefits and have a promising future. However, these technologies are also inescapably exploited to carry out some serious crimes that may harm people [47].
Machine Learning (ML): One AI method, Machine Learning (ML), uses a system that can learn independently through experience. It is utilized for AI reasons, such as mimicking human behavior, and to reduce the time and effort humans require to do even the most straightforward jobs [48]. ML can be considered a system that can learn from examples and experience instead of programming. As a result, a system is said to be using Machine Learning (ML) if it continuously learns and bases decisions on data rather than programming. ML is a brand-new technology being created for business and science that offers new computer functionalities. ML is the foundation of many autonomous engineering, robotics, and medicine solutions. [49].
Approaches to machine learning forensics: Inductive reasoning and deductive reasoning are typically used to define machine learning forensics:
Inductive learning: A broad understanding of particular information is the foundation for inductive reasoning. The acquired information is fresh and does not uphold the truth. This implies that new information might render old knowledge useless. There isn't a solid hypothesis. This field has several objectives, including the need to deduce general principles from a small number of cases. The examples are called experience. This works by looking for qualities that are shared by instances. These use inductive learning-based techniques [50].
Deductive learning: Deductive reasoning draws its knowledge from logically sound, time-tested processes. Deductive reasoning concludes the information by using tried-and-true techniques. The data is nothing new. But the basic knowledge already contains it. Further information cannot invalidate the knowledge that has already been acquired and its foundation in mathematical logic. [51].
Blockchain Technology for Evidence Integrity
To preserve system integrity and guarantee the accuracy of the evidence for admission in court, electronic evidence must be shielded against modification or deletion. Information validity must be ensured through the Chain of Custody [52]. Blockchain technology, a decentralized network used for Bitcoins and other currencies, may provide a secure database by hashing data and storing it in blocks. By integrating blockchain technology into the Chain of Custody procedure, monitoring accesses and guaranteeing the validity of data presented in court will be possible. The potential of blockchain technology to sectionalize thorough reads of transactions back to inception offers the rhetorical community enormous promise [53]. It is essentially a distributed information system that maintains a continuously expanding tamper-proof block structure that includes batches of individual transactions. Initially developed for Bitcoin money, it creates a decentralized, fully replicated append-only ledger in a peer-to-peer network.
The catalogue, cryptography, consensus, and business logic are duplicated aspects of Blockchain [54]. An increasing collection of records is the Blockchain. Blockchain developed in 2008 with the creation of Bitcoin. The financial sector, the government, the media, the law, and the arts are just a few of the industries that stand to be impacted by this.
The ledger or records are shared across several users or nodes on peer-to-peer networks. Depending on whether network nodes need permission to serve as verifiers, the Blockchain may be divided into many subcategories [5]. Each block in Blockchain comprises a safe hash of the block before it, the block after it, and the timestamp. If someone attempts to edit the current data, the hash value changes, and the chain collapses [55]. Records are added to the Blockchain with the prior hash value (Figure 2).
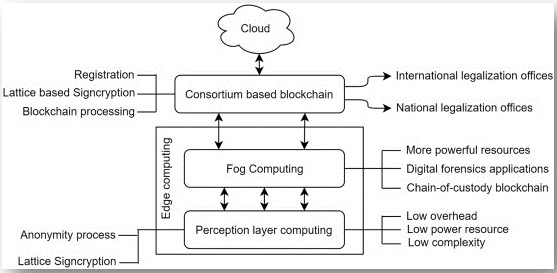
Figure 2:
Blockchain is the ideal option for keeping and protecting the forensic Coc since it offers the finest security, integrity, transparency, and audit. Due to the distributed nature of the Blockchain, which makes it challenging to change any one block, it reduces disputes and fosters more confidence. The best CoC option for the digital age of forensics is Blockchain [56].
Challenges and Risks in Ensuring Quality Control in Digital Forensics Investigations
Digital forensics plays a pivotal role in modern investigative practices, necessitating the utmost attention to quality control to ensure the accuracy, reliability, and integrity of evidence collected and analyzed. This scientific paper systematically examines digital forensics' critical challenges and potential risks [57]. These challenges include keeping pace with rapidly evolving technology, addressing encryption and data protection barriers, countering anti-forensic techniques, managing the vast volume of digital data, ensuring a secure chain of custody, handling sensitive information in compliance with privacy laws, dealing with resource limitations in forensic laboratories, tackling the absence of global standards, and addressing the complexities of investigating Internet of Things (IoT) devices and cross-border data [58]. Additionally, this paper presents a series of evidence-based strategies to mitigate these challenges and enhance quality control in digital forensics investigations. Quality control is a fundamental aspect of digital forensics, guaranteeing the accuracy and reliability of evidence. This scientific paper aims to identify and explore the key obstacles and risks that digital forensics practitioners encounter during investigations.
Evolving Technology
Digital forensics investigations must adapt to the fast-paced evolution of technology, including new operating systems, software, and communication platforms. Regular skill updates and equipment upgrades are vital for analysts to effectively handle the latest digital gadgets and data formats [59].
Encryption and Data Protection
The proliferation of encrypted data and secure communication technologies poses substantial hurdles for digital forensics investigators. The lack of access to encryption keys or passwords may hinder the acquisition of crucial evidence, affecting the overall effectiveness of investigations [60].
Anti-Forensic Techniques
Perpetrators of digital crimes employ anti-forensic methods to conceal or erase evidence. These tactics, such as data wiping, file obfuscation, and steganography, present significant challenges for data recovery and analysis [61].
Data Volume and Complexity
The ever-increasing volume of data stored in digital devices poses challenges for investigators. The complexity of digital storage systems can result in data fragmentation and other difficulties, impacting the successful recovery and analysis of pertinent information [62].
Chain of Custody
Maintaining a secure and unbroken chain of custody for digital evidence ensures its admissibility in court. Mishandling or inadequate documentation can compromise the integrity and reliability of the evidence [63].
Privacy and Legal Concerns
Digital forensics investigations often involve accessing sensitive and private information. Striking a balance between investigative needs, privacy considerations, and adherence to applicable laws and regulations is complex [64].
Resource Limitations
Digital forensics laboratories may face resource constraints regarding workforce, budget, and equipment. These limitations can impede investigations' pace and quality [65].
Lack of Standardization
The absence of global standards and best practices in digital forensics results in varied methodologies and reporting, affecting investigations' quality and reliability [66].
Expertise and Training
Skilled and experienced digital forensic analysts are pivotal to maintaining quality control. The scarcity of qualified professionals may lead to subpar investigations and inaccurate findings [67].
Internet of Things (IoT) Devices
As the IoT continues to grow, many gadgets become potential sources of digital evidence. Investigating data from IoT devices poses unique challenges due to their diversity, proprietary protocols, and limited forensic tools [68].
Cross-Border Challenges
Digital forensics investigations involving data stored in multiple countries face legal, cultural, and logistical obstacles. Critical challenges include obtaining sufficient legal authorization and navigating international data protection regulations [69].
Mitigation Strategies
This section provides evidence-based strategies to address the identified challenges, including continuous training and certification for digital forensics personnel, establishment of robust standard operating procedures, collaboration with relevant stakeholders, and leveraging technological advancements [70].
Ensuring quality control in digital forensics is a multifaceted endeavour, indispensable for the reliability and admissibility of evidence. By comprehensively addressing the identified challenges and adopting appropriate strategies, digital forensics practitioners can improve their investigations' quality and effectiveness.
Ethical and Legal Considerations
Ethical and legal considerations are paramount in digital forensics, where investigators deal with sensitive data and potential privacy infringements.
Adherence to ethical principles and compliance with relevant laws and regulations are essential to maintain the credibility and integrity of digital forensic investigations [71]. This section explores critical ethical and legal considerations in digital forensics.
Privacy and Data Protection
Respecting individuals' privacy rights is a fundamental ethical principle in digital forensics. Investigators must handle personal and sensitive data with utmost care, ensuring that it is collected, analyzed, and stored securely. Compliance with data protection laws and regulations, such as the General Data Protection Regulation (GDPR), is crucial in safeguarding the rights of data subjects [72].
Informed Consent
In some cases, digital forensic investigations may involve accessing personal devices or accounts belonging to individuals who are not suspects. Obtaining informed consent from the owners before accessing their data is an ethical requirement unless legally exempted [73].
Impartiality and Objectivity
Digital forensic analysts must maintain impartiality and objectivity throughout the investigation process. Avoiding biases and ensuring that their findings are based on scientific principles and evidence help uphold the credibility of their work [74].
Chain of Custody
Maintaining an unbroken chain of custody is an ethical obligation and a legal requirement. Properly documenting evidence handling, transfer, and storage ensures its integrity and admissibility in court [75].
Disclosure of Findings
Clear and transparent reporting of findings is essential. Digital forensic analysts must accurately document their methodologies, assumptions, limitations, and conclusions to allow stakeholders to make informed decisions [76].
Conflict of Interest
Identifying and disclosing potential conflicts of interest is crucial to maintain integrity and prevent compromise in the investigation process [77].
Admissibility in Court
Ensuring digital evidence is collected and handled following legal requirements is critical for its admissibility in court. Failure to comply with legal procedures may make evidence in admissible [78].
Cross-Border Considerations
Digital forensics investigations may involve data held in multiple jurisdictions. Investigators must comply with international data protection and privacy laws [79].
Retention and Destruction of Data
Retaining digital evidence beyond the required period or failing to properly dispose of data after the investigation may lead to potential privacy breaches. Proper data retention and destruction practices are essential [80].
Continuous Professional Development
Through continuous professional development, digital forensic analysts must stay updated on emerging technologies, legal developments, and ethical standards. Ongoing training ensures their skills remain current and relevant [81]. Ethical and legal considerations are foundational principles in digital forensics. Adhering to these principles not only upholds the integrity and credibility of investigations but also protects individuals' rights and privacy.
As technology and legal landscapes evolve, digital forensic practitioners must remain vigilant in addressing ethical challenges and complying with relevant laws to maintain the highest standards of conduct and professionalism in their field.
Conclusion
In conclusion, digital forensic investigations will continue to play a pivotal role in addressing cybercrime and ensuring justice. Embracing best practices and integrating emerging technologies will empower digital forensic professionals to maintain the highest quality control standards, making their findings more robust and reliable for legal proceedings and societal trust. By staying ahead of technological advancements and continuously evolving methods, digital forensic teams can navigate the ever-changing digital landscape and fulfill their critical role in securing cyberspace. Ensuring quality control in digital forensic investigations is paramount in today's digital age. The complexity and prevalence of digital evidence make establishing robust and reliable best practices for conducting investigations essential. Throughout this study, we have explored various key factors that contribute to maintaining quality control in the digital forensic process. By following the best practices discussed, such as adherence to industry standards, maintaining chain of custody, employing skilled and certified professionals, conducting thorough documentation, and leveraging validation and peer review, digital forensic teams can enhance the integrity and credibility of their findings. These practices not only bolster the reliability of evidence in legal proceedings but also increase public trust in the digital forensic community.
References
- Stoykova R, Franke K. Standard representation for digital forensic processing 13th International Conference on Systematic Approaches to Digital Forensic Engineering (SADFE), New York, USA. 2020; 2020: 46-56.
- Tully G, Cohen N, Compton D, Davies G, Isbell R, Watson T. Quality standards for digital forensics: learning from experience in England & Wales. Forensic Science International: Digital Investigation. 2020; 32: 200905.
- Tully G, Cohen N, Compton D, Davies G, Isbell R, Watson T. Quality standards for digital forensics: learning from experience in England & Wales. Forensic science international. Digit Investig. 2020; 32: 200905.
- Rappert B, Wheat H, Wilson-Kovacs D. Rationing bytes: managing demand for digital forensic examinations. Policing Soc. 2021; 31: 52-65.
- Casey E, Barnum S, Griffith R, Snyder J, van Beek H, Nelson A. Advancing coordinated cyber-investigations and tool interoperability using a community developed specification language. Digit Investig. Sep 2017; 22: 14-45.
- PCAST releases report on forensic science in criminal courts. whitehouse.gov [online]. Available from: https://obamawhitehouse.archives.gov/blog/2016/09/20/pcast-releases-report-forensic-science-criminal-courts.
- Horsman G, Sunde N. Unboxing the digital forensic investigation process. Sci Justice. 2022; 62: 171-80.
- Ariffin KAZ, Ahmad FH. Indicators for maturity and readiness for digital forensic investigation in era of Industrial Revolution 4.0. Comput Sec. 2021; 105: 102237.
- Bulbul HI, Yavuzcan HG, Ozel M. Digital forensics: an analytical crime scene procedure model (ACSPM). Forensic Sci Int. 2013; 233: 244-56.
- Horsman G. Digital evidence strategies for digital forensic science examinations. Sci Justice. 2023; 63: 116-26.
- Nsiah Amoako EN, McCartney C. Swapping Carrots for Sticks: forensic science provider views of the Forensic Regulator Act 2021. Sci Justice. 2022; 62: 506-14.
- Sunde N. Strategies for safeguarding examiner objectivity and evidence reliability during digital forensic investigations. Forensic science international. Digit Investig. 2022; 40: 301317.
- Horsman G. ’Scaffolding’ responses to digital forensic inquiries. Wiley Interdiscip Rev Forensic Sci. 2022; 4: e1451.
- Bhat WA, AlZahrani A, Wani MA. Can computer forensic tools be trusted in digital investigations? Sci Justice. 2021; 61: 198-203.
- Humphries G, Nordvik R, Manifavas H, Cobley P, Sorell M. Law Enforcement educational challenges for mobile forensics. Forensic science international. Digit Investig. 2021; 38: 301129.
- Al-Khateeb, Haider, Gregory Epiphaniou, Herbert Daly. Blockchain for modern digital forensics: the chain-of-custody as a distributed ledger Blockchain and Clinical Trial: Securing Patient Data. 2019: 149-68.
- Horsman G. Tool testing and reliability issues in the field of digital forensics. Digit Investig. 2019; 28: 163-75.
- Abuosba K. Formalizing big data processing lifecycles: acquisition, serialization, aggregation, analysis, mining, knowledge representation, and information dissemination. 2015; 1-4.
- Alhaboby ZA, Al-Khateeb HM, Barnes J, Short E. The language is disgusting and they refer to Short E. my disability: the cyberharassment of disabled people. Disabil Soc. 2016; 31: 1138-43.
- Alhaboby ZA, Alhaboby D, Al-Khateeb HM, Epiphaniou G, Ismail DKB, Jahankhani H, et al. Understanding the cyber-victimisation of people with long term conditions and the need for collaborative forensics-enabled disease management programmes. In: Jahankhani H, editor. Cyber criminology. Advanced sciences and technologies for security applications. Cham: Springer. 2018; 227-50.
- Moffatt-Bruce SD, Ferdinand FD, Fann JI. Patient safety: disclosure of medical errors and risk mitigation. Ann Thorac Surg. 2016; 102: 358-62.
- Nakamoto S. Bitcoin: a peer-to-peer electronic cash system; 2008. Available from: https://bitcoin.org/bitcoin.pdf.
- Navarro-Ortiz J, Sendra S, Ameigeiras P, Lopez-Soler JM. Integration of LoRaWAN and 4G/5G for the industrial internet of things. IEEE Commun Mag. 2018; 56: 60-7.
- Zhang Y, Xu C, Yu S, Li H, Zhang X. SCLPV: secure certificateless public verification for cloud-based cyber-physical-social systems against malicious auditors. IEEE Trans Comput Soc Syst. Dec 2018; 5: 854-7.
- Liu Y, Hu S. Cyberthreat analysis and detection for energy theft in social networking of smart homes. IEEE Trans Comput Soc Syst. Dec 2015; 2: 148-58.
- Teing Y, Dehghantanha A, Choo KR, Muda Z, Abdullah MT. Greening cloud-enabled big data storage forensics: Syncany as a case study. IEEE Trans Sustain Comput. Apr/Jun 2018; 4: 204-16.
- Paradise A, Shabtai A, Puzis R, Elyashar A, Elovici Y, Roshandel M, et al. Creation and management of social network honeypots for detecting targeted cyber attacks. IEEE Trans Comput Soc Syst. Sep 2017; 4:65-79.
- Hossain M, Karim Y, Hasan R. FIF-IoT: A forensic investigation framework for IoT using a public digital ledger. In: Proceedings of the IEEE international congress internet things (ICIOT). 2018; 33-40.
- Wu S, Chen Y, Wang Q, Li M, Wang C, Luo X. CReam: A smart contract enabled collusion-resistant e-auction. IEEE Trans Inf Forensics Sec. 2019; 14: 1687-701.
- Liu Z, Seo H. Iot-nums: evaluating nums elliptic curve cryptography for iot platforms. IEEE Trans Inf Forensics Sec. 2019; 14: 720-9.
- Zhang Y, Wu S, Jin B, Du J. A blockchain-based process provenance for cloud forensics. Proceedings of the 3rd IEEE international conference. Comput Commun (ICCC). 2017: 2470-3.
- Al-Nemrat A. Identity theft on e-government/e-governance & digital forensics. In: Proceedings of the international symposium program. 2018; 1.
- Ulybyshev D, et al. (WIP) blockhub: Blockchain-based software development system for untrusted environments”. Proceedings of the IEEE 11th int. conf. cloud comput (CLOUD). 2018; 582-5.
- Thomas L. Walmart is quietly preparing to enter the metaverse. Meta (2021) Founder’s Letter. 2022; 2022: 2021 Stephenson, N.: Snow crash: a novel (2003).
- Meta. Founder’s letter, 2021; 2021. Stephenson, N: Snow crash: a novel (2003) [cited 31-1-2022]. Available from: https://about.fb.com/news/2021/10/founders-letter/.
- Meta. The metaverse and how we’ll build it together [cited Jan 31]. Available from: http://youtube.com/watch?v=Uvufun6xer8. Vol. 2022; 2021.
- Leda A. How the metaverse could impact the world and the future of technology [cited Jan 30]. Available from: https://abcnews.go.com/Technology/metaverse-impact-world-future-technology/story?id=82519587. 2022; 2022.
- Satya N. The metaverse is here. Available from: https://twitter.com/satyanadella/status/1455624165201887234. 2022; 2021.
- Tony P. The seven rules of the metaverse. Available from: https://medium.com/meta-verses/the-seven-rules-of-the-metaverse-7d4e06fa864c. 2022; 2021.
- BBC NEWS. Artist’ vandalises’ snapchat’s AR balloon dog sculpture. Available from: https://www.bbc.com/news/technology-41524550. 2022; 2017.
- Sarah P. Roblox responds to the hack that allowed a child’s avatar to be raped in its game. Available from: https://techcrunch.com/2018/07/18/roblox-responds-to-the-hack-that-allowed-a-childs-avatar-to-be-raped-in-its-game/. 2022; 2018.
- Gamespot. Roblox accounts are being hacked to share trump propaganda. Available from: https://www.gamespot.com/articles/roblox-accounts-are-being-hacked-to-share-trump-pr/1100-6479311/. 2022; 2020.
- Kent K, Chevalier S, Grance T, Dang H. Guide to integrating forensic techniques into incident response. NIST Spec Publ. 2006; 10: 800-86.
- Real-time data analytics and the metaverse; 2022. Available from: https://www.nanalyze.com/2021/12/real-time-data-analytics-metaverse/.
- Schjølberg S, Ghernaouti-Helie S. A global protocol on cybersecurity and cybercrime. Cybercrimelaw Net. 2009.
- Krombholz K, Hobel H, Huber M, Weippl E. Advanced social engineering attacks. J Inf Secur Appl. 2015; 22: 113-22.
- Falchuk B, Loeb S, Neff R. The social metaverse: battle for privacy. IEEE Technol Soc Mag. 2018; 37: 52-61.
- Laue C. Crime potential of metaverses. 2011; 19-29.
- Lodder AR. Conflict resolution in virtual worlds: general characteristics and the 2009 Dutch convictions on virtual theft. 2011; 79-93.
- Cavaliere L. VOMA: the world’s First Entirely Online Art Museum. Available from: https://voma.space/about-us/. 2022; 2021.
- Google arts and culture; 2021. A new way of experiencing art and culture. Available from: https://about.artsandculture.google.com//. 2022.
- Jordanoska A. The exciting world of nfts: a consideration of regulatory and financial crime risks. Butterworths J Int Bank Finac Law. 2021; 10: 716.
- Rebecca O. Roblox: easy ways to get robux. Available from: https://www.thegamer.com/roblox-ways-to-get-robux/. 2022; 2022.
- Rishav D. How to hack in Roblox 2022 for free and in easy steps?. Available from: https://www.phoneswiki.com/how-to-hack-roblox/. 2022; 2022.
- Jung S, Seo S, Kim Y, Lee C. Memory layout extraction and verification method for reliable physical memory acquisition. Electronics. 2021; 10: 1380.
- Tran SDP, Seok B, Lee C. Hanmre - an authenticated encryption secure against side-channel attacks for nonce-misuse and lightweight approaches. Appl Soft Comput. 2020; 97: 106663.
- Seok B, Lee C. Fast implementations of arx-based lightweight block ciphers (sparx, cham) on 32-bit processor. Int J Distrib Sens Netw. 2019; 15: 1550147719874180.
- Article Google Scholar.
- Ebert LC, Nguyen TT, Breitbeck R, Braun M, Thali MJ, Ross S. The forensic holodeck: an immersive display for forensic crime scene reconstructions. Forensic Sci Med Pathol. 2014; 10: 623-6.
- Dean T. The ethics of the metaverse. Available from: https://venturebeat.com/2022/01/26/the-ethics-of-the-metaverse-2/. 2022; 2022.
- Davic B. Ethical implications posed by the Metaverse. Available from: https://loupedin.blog/2021/12/ethical-implications-posed-by-the-metaverse/. 2022; 2021.
- The New York times. 2022; 2020. F.B.I. asks apple to help unlock two iPhones. Available from: https://www.nytimes.com/2020/01/07/technology/apple-fbi-iphone-encryption.html.
- Nordvik R, Stoykova R, Franke K, Axelsson S, Toolan F. Reliability validation for file system interpretation. Forensic sci int. Digit Investig. 2021; 37: 301174.
- Google Scholar.
- Di Pietro RD, Cresci S. Metaverse: security and privacy issues. In: IEEE International Conference on Trust, Privacy and Security in Intelligent Systems, and Applications (IEEE TPS). 2021.
- Jeremy B. Current and future xr risks include: the vast tracking of consumers and bystanders–including their sensitive information–manipulation and abuse of digital identities, cyberharassment, and more. In: Augmented reality + virtual reality-privacy & autonomy considerations in emerging, immersive digital worlds. Future of privacy forum. 2021; 15-21.
- Pfeuffer K, Geiger MJ, Prange S, Mecke L, Buschek D, Alt F. Behavioural biometrics in vr: identifying people from body motion and relations in virtual reality. In: Proceedings of the 2019 CHI conference on human factors in computing systems. 2019; 1-12.
- Zarepour E, Hosseini M, Kanhere SS, Sowmya A. A context-based privacy preserving framework for wearable visual lifeloggers. In: IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops). 2016; 2016: 1-4.
- Reilly D, Salimian M, MacKay B, Mathiasen N, Edwards WK, Franz J. Secspace: prototyping usable privacy and security for mixed reality collaborative environments. In: Proceedings of the 2014 ACM SIGCHI symposium on engineering interactive computing systems. 2014; 273-82.
- Kruk ME, Gage AD, Joseph NT, Danaei G, García-Saisó S, Salomon JA. Mortality due to low-quality health systems in the universal health coverage era: a systematic analysis of amenable deaths in 137 countries. Lancet. 2018; 392: 2203-12.
- Kruk ME, Freedman LP, Anglin GA, Waldman RJ. Rebuilding health systems to improve health and promote statebuilding in post-conflict countries: a theoretical framework and research agenda. Soc Sci Med. 2010; 70: 89-97.
- Kruk ME, Gage AD, Arsenault C, Jordan K, Leslie HH, Roder-DeWan S, et al. High-quality health systems in the Sustainable Development Goals era: time for a revolution. Lancet Glob Health. 2018; 6: e1196-252.
- Black RE, Liu L, Hartwig FP, Villavicencio F, Rodriguez-Martinez A, Vidaletti LP, et al. Health and development from preconception to 20 years of age and human capital. Lancet. 2022; 399: 02533-2.
- Victora CG, Hartwig FP, Vidaletti LP, Martorell R, Osmond C, Richter LM, et al. Effects of early-life poverty on health and human capital in children and adolescents: analyses of national surveys and birth cohort studies in LMICs. Lancet. 2022; 399: 1741-52.
- Vaivada T, Lassi ZS, Irfan O, Salam RA, Das JK, Oh C, et al. What can work and how? An overview of evidence-based interventions and delivery strategies to support health and human development from before conception to 20 years. Lancet. 2022; 399: 1810-29.
- Lawn JE, Blencowe H, Waiswa P, Amouzou A, Mathers C, Hogan D, et al. Stillbirths: rates, risk factors, and acceleration towards 2030. Lancet. 2016; 387: 587-603.
- Black MM, Walker SP, Fernald LCH, Andersen CT, DiGirolamo AM, Lu C, et al. Early childhood development coming of age: science through the life course. Lancet. 2017; 389: 77-90.
- Britto PR, Lye SJ, Proulx K, Yousafzai AK, Matthews SG, Vaivada T, et al. Nurturing care: promoting early childhood development. Lancet. 2017; 389: 91-102.
- Richter LM, Daelmans B, Lombardi J, Heymann J, Boo FL, Behrman JR, et al. Investing in the foundation of sustainable development: pathways to scale up for early childhood development. Lancet. 2017; 389: 103-18.
- Olusanya BO, Davis AC, Wertlieb D, et al. Developmental disabilities among children younger than 5 years in 195 countries and territories, 1990-2016: a systematic analysis for the Global Burden of Disease Study 2016. Lancet Glob Health. 2018; 6: e1100–21.
- Lu C, Black MM, Richter LM. Risk of poor development in young children in low-income and middle-income countries: an estimation and analysis at the global, regional, and country level. Lancet Glob Health. 2016; 4: e916-22.